
Fortifying Your Defenses: 10 Essential Cybersecurity Tools for Small Businesses
In modern day virtual international, small companies are at a developing risk of cyberattacks. Lack of sources and information regularly go away them at risk of sophisticated threats. However, making an investment within the right cybersecurity tools can immensely improve their defense capabilities and guard valuable statistics. That's why we've compiled a listing of 10 important cybersecurity equipment every small commercial enterprise ought to bear in mind. From firewalls and antivirus software program to penetration checking out equipment, those answers can help beef up your protection posture and save you unauthorized get right of entry to. Network monitoring gear are essential for detecting any suspicious sports in real-time and responding directly. Encryption tools can shield touchy information both at rest and in transit, ensuring information confidentiality. Implementing multi-element authentication adds an additional layer of safety with the aid of requiring a couple of kinds of verification.
By prioritizing cybersecurity and leveraging these gear efficiently, small companies can notably reduce the chance of falling sufferer to cybercrime. Stay one step beforehand of cyber adversaries with robust cybersecurity measures in region. Don't wait until it is too past due – guard your commercial enterprise now!
1. Antivirus Software: Cyber Security Tools
Antivirus software program program is here to maintain the day! Acting because the cornerstone of your cybersecurity technique, this powerful tool works tirelessly to defend your structures from malicious threats. With its non-stop scanning competencies, it swiftly detects and eliminates malware, viruses, and other dangerous software program. By deploying antivirus software program application, you may make certain the integrity of your data and hold the easy operation of your gadgets. Say good-bye to cyber threats wreaking havoc on your structures! This critical cybersecurity tool stands guard 24/7, maintaining your statistics secure from functionality breaches. Embrace the power of antivirus software as your frontline protection in competition to cyberattacks.
Don't wait any further – pork up your structures with this critical cybersecurity tool in recent times and enjoy peace of thoughts understanding that your information is steady from outside threats.

2. Firewall
Cybersecurity tools like firewalls are your first line of protection within the ever-evolving digital landscape. Acting as a digital barrier, firewalls meticulously display the flow of facts entering into and exiting your network. With custom designed safety guidelines in area, they're capable of rapidly block malicious content material fabric and unauthorized get right of entry to tries. By proactively safeguarding your community, firewalls protect your sensitive statistics from cyber threats.
These effective gear work tirelessly behind the curtain, reading website visitors styles and figuring out suspicious behavior in real-time. By doing so, they help prevent potential breaches and restriction the impact of any cyber assaults. Their function is important in keeping the integrity and protection of your virtual infrastructure. Implementing firewalls is a proactive step toward fortifying your defenses in competition to cyber threats and ensuring a robust cybersecurity posture.
3. Virtual Private Network (VPN)
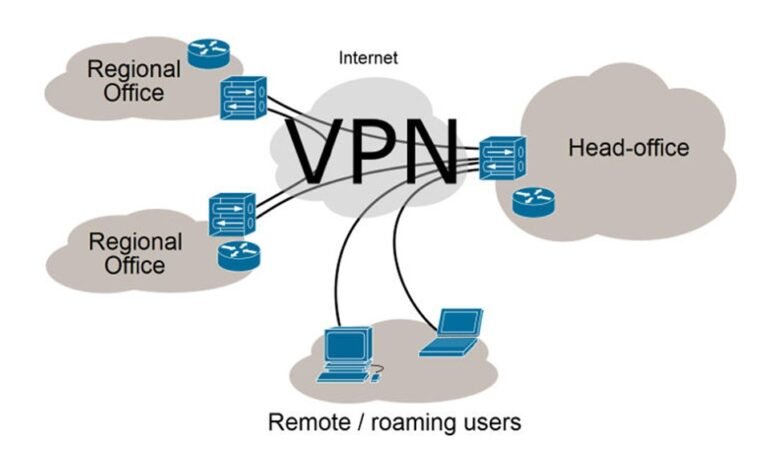
Cybersecurity equipment like VPNs are a game-changer for far off employees! They provide a stable manner to get right of entry to business enterprise assets from everywhere, even outside the place of job. By encrypting net connections, VPNs ensure that each one communique and statistics transfers are included from cyber threats on public networks. This method your touchy statistics stays steady from prying eyes and cybercriminals who can also attempt to intercept it. Using a VPN gives a similarly layer of security whilst operating remotely, offering you with peace of thoughts knowledge that your crucial data is encrypted and regular. It's like having a virtual bodyguard protecting your on line interest and communications. With the rise of far off paintings, having a VPN has end up important for keeping the privateness and safety of business enterprise facts.
In era of digital age, in which cyber threats are constantly evolving, having cybersecurity equipment like VPNs isn't always certainly recommended but essential. The peace of thoughts and protection furnished by a VPN make it a need to-have for everybody operating remotely or gaining access to sensitive organization resources online. Don't depart your records susceptible – take benefit of these effective cybersecurity equipment to live secure within the virtual world!
4. Password Manager
Cybersecurity gear like password managers are a sport-changer for small groups seeking to enhance their online safety. Weak and reused passwords are not any healthful for the sturdy and specific passwords generated through the ones gear. By securely storing those passwords, the chance of unauthorized get right of entry to and credential theft is drastically decreased. This way plenty less strain and fear for small agencies as they navigate the virtual landscape. Password managers ensure that every account is prepared with a strong protection towards cyber threats, offering peace of thoughts for users. With cyber attacks on the rise, having reliable safety features in vicinity is crucial. Embracing password managers can significantly pork up a collection's on line defenses and preserve touchy records stable from malicious factors.
5. Secure Email Gateway
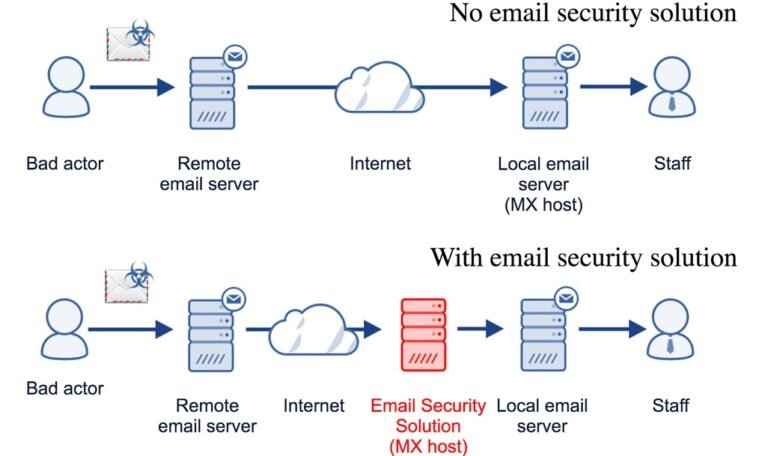
Cybersecurity equipment preserve to evolve, presenting a protect in competition to the ever-gift threat of cyber assaults. One essential device in the arsenal is the e-mail gateway - a stalwart mother or father within the realm of digital communication. By filtering both inbound and outbound emails, this cybersecurity champion adeptly thwarts malicious attachments, suspicious hyperlinks, and direct mail messages from infiltrating your inbox.
With its sturdy defenses in region, the e-mail gateway ensures a strong communication environment wherein threats are rapidly neutralized. Its vigilant stance in competition to phishing scams and malware distribution serves as a bulwark defensive touchy information and private facts from falling into the incorrect arms. The reliability and performance of the e-mail gateway make it an essential asset for corporations, organizations, and those navigating present day-day complicated cyber panorama.
Incorporating superior algorithms and actual-time scanning competencies, this important cybersecurity tool stands as a reassuring sentinel status protect over your virtual correspondence. Take comfort in understanding that your e mail communications are shielded by using a steadfast fortress dedicated to keeping the integrity of your on line interactions.
6. Intrusion Detection and Prevention System (IDPS)
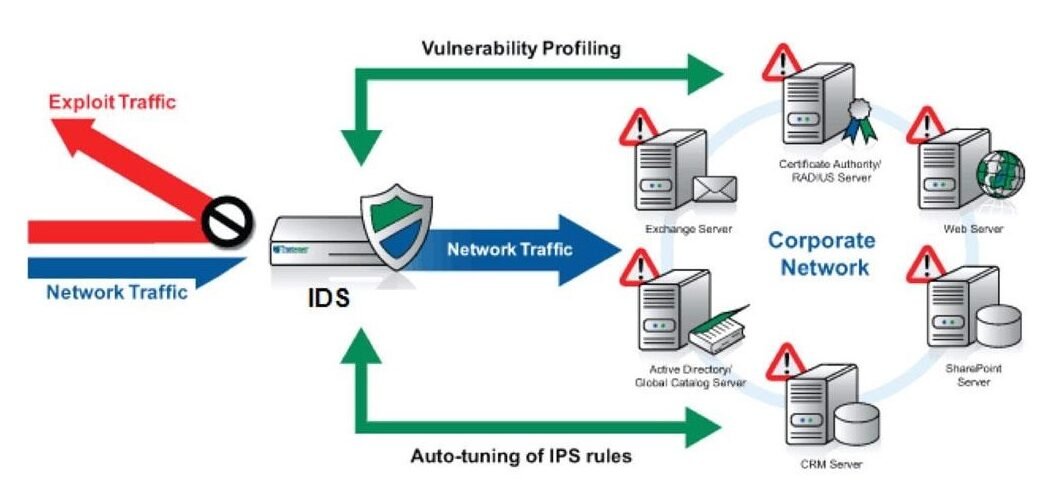
Imagine having a powerful cybersecurity device at your disposal that continuously monitors and analyzes each tourist in your website. The Intrusion Detection and Prevention System (IDPS) video show does definitely that, alerting you of any suspicious sports activities or symptoms of capacity safety breaches.
This superior device works by using way of detecting unauthorized get admission to attempts, malware infections, and each different anomalies in actual-time. By rapidly responding to these threats, the IDPS permits prevent protection breaches from escalating and causing huge damage to your net website online. With the IDPS in vicinity, you can live one step earlier of cybercriminals by means of the use of proactively figuring out and mitigating safety risks. This present day generation provides peace of mind knowing that your net web site is safeguarded in competition to evolving cyber threats.
7. Web Application Firewall (WAF)
Imagine having a effective cybersecurity tool at your disposal that constantly monitors and analyzes each vacationer on your net web site. The Intrusion Detection and Prevention System (IDPS) video display does actually that, alerting you of any suspicious sports or symptoms and signs and symptoms of potential protection breaches.
This advanced device works via detecting unauthorized get right of entry to tries, malware infections, and every other anomalies in actual-time. By hastily responding to those threats, the IDPS enables save you safety breaches from escalating and inflicting splendid harm in your net website. With the IDPS in location, you can stay one step in advance of cybercriminals through the use of proactively identifying and mitigating protection dangers. This progressive era affords peace of thoughts knowledge that your internet site is safeguarded towards evolving cyber threats.
8. Data Backup and Recovery Solution
Imagine having a effective cybersecurity tool at your disposal that constantly monitors and analyzes each vacationer on your net web site. The Intrusion Detection and Prevention System (IDPS) video display does actually that, alerting you of any suspicious sports or symptoms and signs and symptoms of potential protection breaches.
This advanced device works via detecting unauthorized get right of entry to tries, malware infections, and every other anomalies in actual-time. By hastily responding to those threats, the IDPS enables save you safety breaches from escalating and inflicting splendid harm in your net website. With the IDPS in location, you can stay one step in advance of cybercriminals through the use of proactively identifying and mitigating protection dangers. This progressive era affords peace of thoughts knowledge that your internet site is safeguarded towards evolving cyber threats.
9. Endpoint Security Solutions
Protecting your endpoints, together with laptops, computer systems, and cell gadgets, is essential in current-day far off paintings panorama. With the growing range of cyber threats, having sturdy endpoint safety solutions is a have to. These equipment offer a huge type of safety abilities to shield in competition to malware, ransomware, and different malicious assaults.
They ensure that your devices are secure every inside and outside the organization network. By implementing endpoint protection answers, you may proactively guard sensitive records and mitigate capability risks.
This technology affords real-time hazard intelligence and continuous tracking to pick out and block any suspicious sports.With the ever-evolving cybersecurity landscape, staying ahead of threats is important for groups of all sizes. Endpoint safety equipment come up with peace of mind understanding that your gadgets are protected towards cyber threats 24/7. Embrace the strength of these system to reinforce your cybersecurity posture and shield your precious belongings from unauthorized access.
10. Security Awareness Training
Employee schooling in cybersecurity equipment is a crucial part of any corporation's protection toward cyber threats. These applications equip personnel with the knowledge and abilities to understand and reply to potential protection incidents. By mastering approximately the present day cybersecurity equipment, employees can proactively protect sensitive information and mitigate dangers.
Through safety cognizance schooling, employees come to be adept at the use of several cybersecurity system correctly. They learn how to come across phishing emails, stable their passwords, and shield enterprise networks from malicious attacks. Additionally, they're professional to reply right away and correctly if a protection breach takes region, minimizing capability harm.
By making an investment in cybersecurity training for personnel, companies can enhance their not unusual security posture and reduce the hazard of a success cyber assaults. Providing non-stop schooling updates guarantees that employees live knowledgeable about evolving cyber threats and fine practices for protective employer assets.

Conclusion
Investing in critical cybersecurity gear is a exercise-changer for small companies seeking to stay ahead of cyber threats. These equipment act as your virtual armor, protective your company from capability assaults that could critically disrupt operations. By combining the ones equipment with strong protection protocols, you create a fortified defense gadget that substantially minimizes the danger of falling sufferer to cybercriminals. Remember, being proactive nowadays method safeguarding your commercial enterprise from high-priced effects tomorrow.
Securing your company with awesome cybersecurity gear is like having a faithful mother or father watching over your digital belongings 24/7. With the right equipment in area, you could navigate the ever-evolving panorama of cyber threats with self-notion and peace of thoughts. Don't anticipate an attack to take area – take manipulate of your cybersecurity now and guard your enterprise from ability vulnerabilities.
FAQ
The costs and features of cybersecurity tools can vary significantly depending on factors such as the size of the business, the level of protection required, and the specific features offered by each vendor. Small businesses should consider conducting a thorough evaluation of their cybersecurity needs and budget constraints before selecting a tool. Additionally, they can explore options such as subscription-based services, which may offer more flexibility in terms of pricing. It’s also important to research customer reviews and testimonials to ensure that the chosen tool meets the business’s requirements and provides adequate protection against cyber threats.
Small businesses should be aware of any regulatory compliance requirements or industry standards relevant to their operations when selecting cybersecurity tools. For example, businesses handling sensitive customer data may need to comply with regulations such as GDPR (General Data Protection Regulation) or HIPAA (Health Insurance Portability and Accountability Act). Choosing tools that are specifically designed to address these compliance requirements can help businesses avoid potential legal and financial repercussions. Additionally, some cybersecurity vendors may offer features or services tailored to specific regulatory frameworks, making it easier for businesses to achieve compliance.
Deploying and managing cybersecurity tools can pose challenges for small businesses, especially those with limited IT resources and expertise. Common obstacles may include difficulties in configuring and integrating different tools, ensuring compatibility with existing systems, and keeping up with software updates and patches. To overcome these challenges, small businesses can consider partnering with managed security service providers (MSSPs) or IT consultants who specialize in cybersecurity. These professionals can provide guidance on selecting and implementing the right tools for the business’s needs and offer ongoing support and maintenance services. Additionally, investing in employee training and education on cybersecurity best practices can help enhance the effectiveness of these tools and minimize the risk of human error or negligence.

